Zero Trust in a Hybrid World
Zero Trust is a bloated term. So are things like eXtended Detection & Response (XDR), Active Cyber Defense (ACD).
Ultimately,
SolarWinds
SolarWinds took the world by surprise, but what made it damaging was the limited knowledge of an adversary jumping from on-premises to the cloud, thanks to Identity and federation of trusts.
Error -7006 on HomePod
If you're privacy conscious, you probably turned on Advanced Data Protection on your Apple account. However, that might leave you in a bad spot with HomePod.
Apple vs Google Ecosystem - Intro
I've wanted to write about this topic for years.
Regardless of how you feel about Apple or Google,
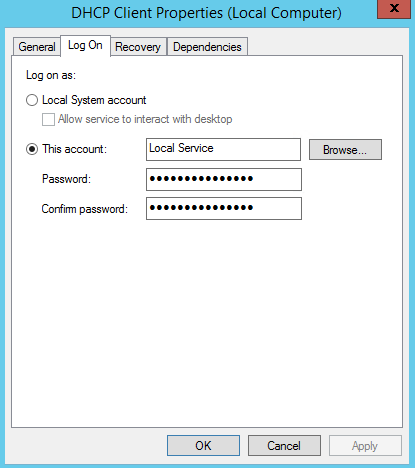
Securing Service Accounts
Learn what Service Accounts should and SHOULD NOT do. It’s one of the best and most fruitful ways to secure things, without the headaches.
Learning Identity Cyber Attacks
Learn the basics, hands on, of identity-based attacks. Become any user, at any time. Bypass smart card. Do recon to build a graph of trust relationships just like the adversary.